Originally published on 460degrees.com
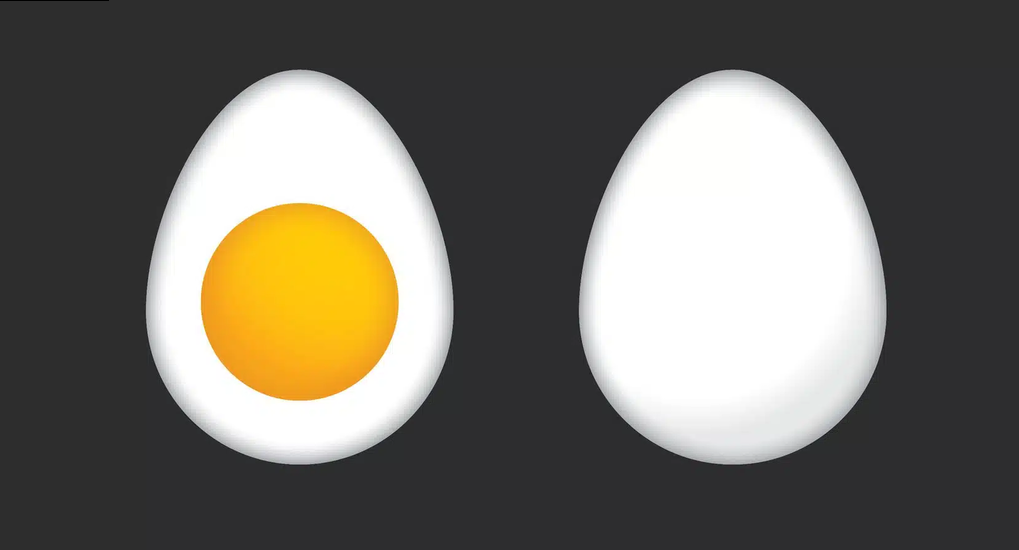
The inside
Your organisation’s sensitive information is like the inside of an egg.
All the personnel, endpoints, IP, stored data and anything else of value is the egg white, with the yolk the most valuable information, such as passwords. Any information that could be attractive to cyber threat actors is like this gooey interior: dynamic, soft, and dependent on protective casing for safety and structural integrity.
The shell
On the outside is the ‘hard shell’ of your cyber security infrastructure. This includes your firewalls, honeypots, network and application security, and more. Combined, these technologies form a protective barrier around your organisation’s vulnerable and valuable contents.

HOW IS YOUR ‘EGG’ UNDER THREAT?
To ensure their security against cyber attacks, most organisations today add layers of protection, constantly updating and investing in different methods to improve the protective properties of their ‘eggshell’.
Cyber security experts know, however, that no shell is perfect. This protective shell can be cracked, peeled away or otherwise bypassed, ultimately leaving your organisational ‘insides’ exposed.
No infrastructure will be effective unless these security technologies are understood and adopted by the people it is meant to protect. So people – your people – are crucial to your organisation’s cyber security approach.
CYBER-SOCIOLOGY AND YOUR PEOPLE
Cyber-Sociology works with the weaknesses and strengths of your people to achieve a stronger security posture in your business.

Cyber-sociology seeks to change the properties of the egg’s contents so that your business is less vulnerable and less dependent on the eggshell for security.
Since we know that the eggshell will inevitably be breached, your people must be able to repel any attacks individually. If we demystify and increase cyber literacy and instil an intrinsic motivation to cultivate a security culture, then the threats presented by cyber threat actors are diminished. Any social engineering and vulnerabilities created by human errors are dramatically reduced.
NO CYBER SECURITY STRATEGY IS PERFECT – BUT IT CAN BE VASTLY IMPROVED
It is important to recognise that once it has been hard-boiled, the egg still needs its shell.
A balance must be struck between strengthening both your human and technological capabilities. We must remember that our eggshell is still a critical deterrent to and shield from cyber attackers. The better maintained our firewalls and network security, the harder we are to ‘crack’.
And even if these outer defences are breached, we can still learn from our mistakes, educate our people and more efficiently and knowledgeably use our cyber security technology.
Cyber-sociology is a paradigm shift away from the conventional approach of layered technologies. It requires a shift in thinking and strategy. With a more human-centred approach, cyber-sociology offers new ways to efficiently use the infrastructure you already have in place and achieve a superior security posture at the same time.
To find out more about CyberBite, and how it can help your organisation, please contact us.